ML models have recommended themselves as a powerful tool for cyberdefense. AI/ML is heavily used in antiviruses (EDR), Next-Gen Firewalls, and SIEM (SOAR) solutions to solve the classification problem as well as to discover anomalous behavior that may indicate a presence of an attacker with the help of Supervised and Unsupervised Learning. Deep Learning helps to filter spam emails and mark fake news to protect users against disinformation [1].
So what about AI in security testing such as penetration and anti-malware testing? The interesting application of AI can be found in the work called ‘Autonomous Penetration Testing using Reinforcement Learning’ by J. Schwartz from the University of Queensland [2] where he proposes to use Reinforcement Learning (RL) for network penetration testing to find the optimal attack path.
We decided to investigate the capabilities of applying ML in testing anti-ransomware solutions. In particular, RL has been chosen for generating ransomware models and finding the optimal test strategy to bypass an anti-ransomware solution.
RL is well known as the way to train a computer to play strategy games. For example, AlphaGo, a computer program designed by DeepMind, has established itself as the best Go and chess player in the world as a result of playing many times with other instances of itself to improve its play with RL [3].
Ransomware simulator
demo.
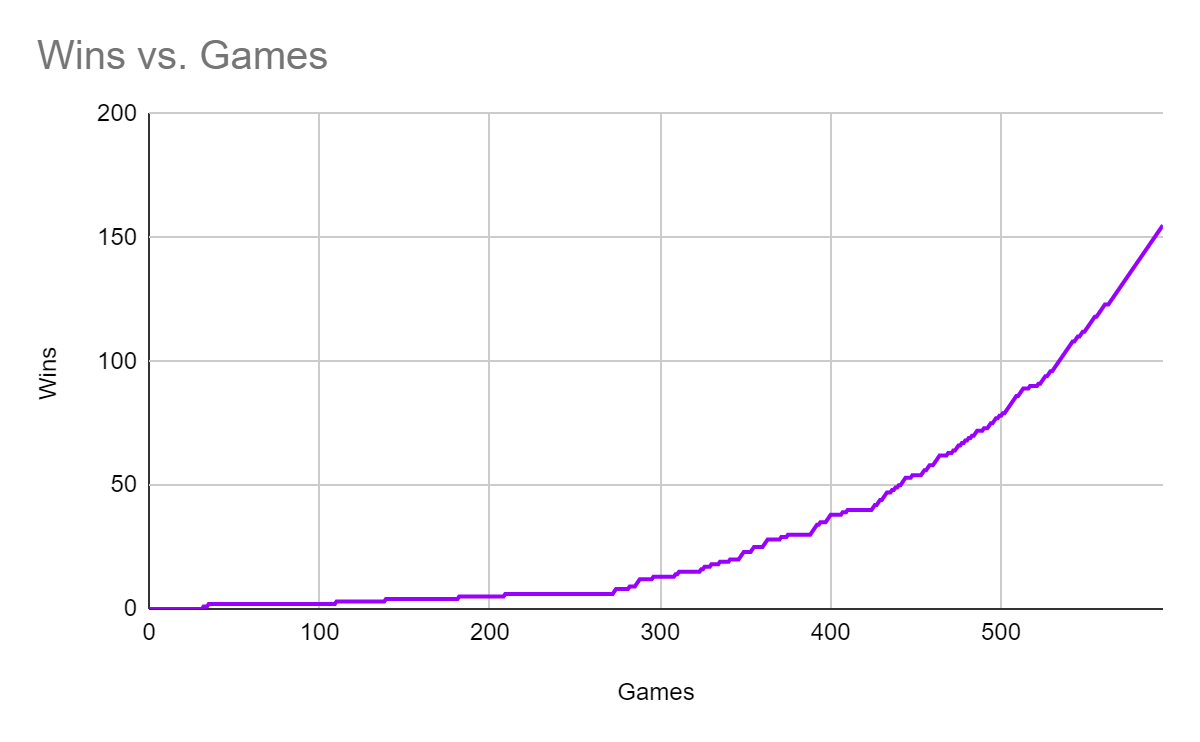
Some of the research results are highlighted below:


| Q (S, A) | States | | | | | | | | Threshold | | |
| Actions | 0 | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | 10 |
| 0 | 3.742632 | 0.787156 | 0.50037 | 0 | 0 | 1.007811 | 0.119928 | 2.686471 | 1.771443 | 0 | all files are encrypted |
| 1 | 7.105196 | 1.013578 | 1.252902 | 0.625865 | 0 | 5.491767 | 0 | 0.110781 | 0.020577 | 0 |
| 2 | 7.545032 | 3.370516 | 1.118979 | 0.296561 | 0 | 1.170941 | 0.170201 | 0.147976 | 0.215866 | 0.763711 |
| 3 | 6.681859 | 1.036887 | 1.431128 | 0 | 0 | 1.178761 | 0.10031 | 0.526232 | 0.019609 | 0.1805 |
| 4 | 3.948145 | 0 | 0 | 0.231532 | 0.120758 | 0.790898 | 0.599471 | 0.871498 | 0.483216 | 0 |
| 5 | 5.816442 | 0 | 1.158697 | 0.693802 | 0 | 1.778738 | 0.715084 | 0.205816 | 0.029846 | 0 |
| 6 | 3.734055 | 8.923577 | 2.616297 | 0 | 0 | 0.747448 | 0.252802 | 0.236518 | 0.020577 | 0 |
| 7 | 7.022468 | 0.056858 | 1.931174 | 0.563466 | 0 | 1.003211 | 0.213173 | 0.198259 | 0.377146 | 0 |
| 8 | 4.158711 | 0.963861 | 1.045184 | 0 | 0 | 0.459586 | 0.590549 | 0.028423 | 0.28698 | 0.01805 |
| 9 | 5.872631 | 0.463353 | 0.387103 | 0 | 1.524341 | 1.143632 | 0.358465 | 0.771859 | 0.112953 | 0.119148 |
| 10 | 5.959267 | 0.9285 | 8.530923 | 1.739734 | 0 | 1.55761 | 0.141551 | 0.244138 | 0.172354 | 0 |
| 11 | 6.141237 | 0 | 0.768712 | 0 | 0.144812 | 1.640483 | 0.149433 | 0.418004 | 0.055891 | 0.068169 |
| 12 | 5.179697 | 1.992647 | 0.713766 | 0 | 0.443053 | 0.652553 | 0.226234 | 0.173608 | 0.372956 | 0.089291 |
| 13 | 3.181544 | 1.945088 | 0.629294 | 0 | 0.422005 | 1.051774 | 2.283579 | 0.231025 | 0.166056 | 0 |
| 14 | 14.11996 | 2.516235 | 1.889826 | 3.106087 | 0.087103 | 0.705648 | 0.275448 | 0.247926 | 0.20654 | 0 |
| 15 | 5.828471 | 0.885469 | 0 | 0.163353 | 0 | 1.260362 | 0.080788 | 0.186429 | 0.010403 | 0.07444 |
References
[1] Attention is All They Need: Combatting Social Media Information Operations With Neural Language Models. FireEye, 2019. Available at https://www.fireeye.com/blog/threat-research/2019/11/combatting-social-media-information-operations-neural-language-models.html
[2] Schwartz J. Autonomous Penetration Testing using Reinforcement Learning. University of Queensland, 2018, available at https://arxiv.org/ftp/arxiv/papers/1905/1905.05965.pdf
[3] Mastering the game of Go without human knowledge. DeepMind, 2017. Available at https://www.nature.com/articles/nature24270.epdf


No comments:
Post a Comment